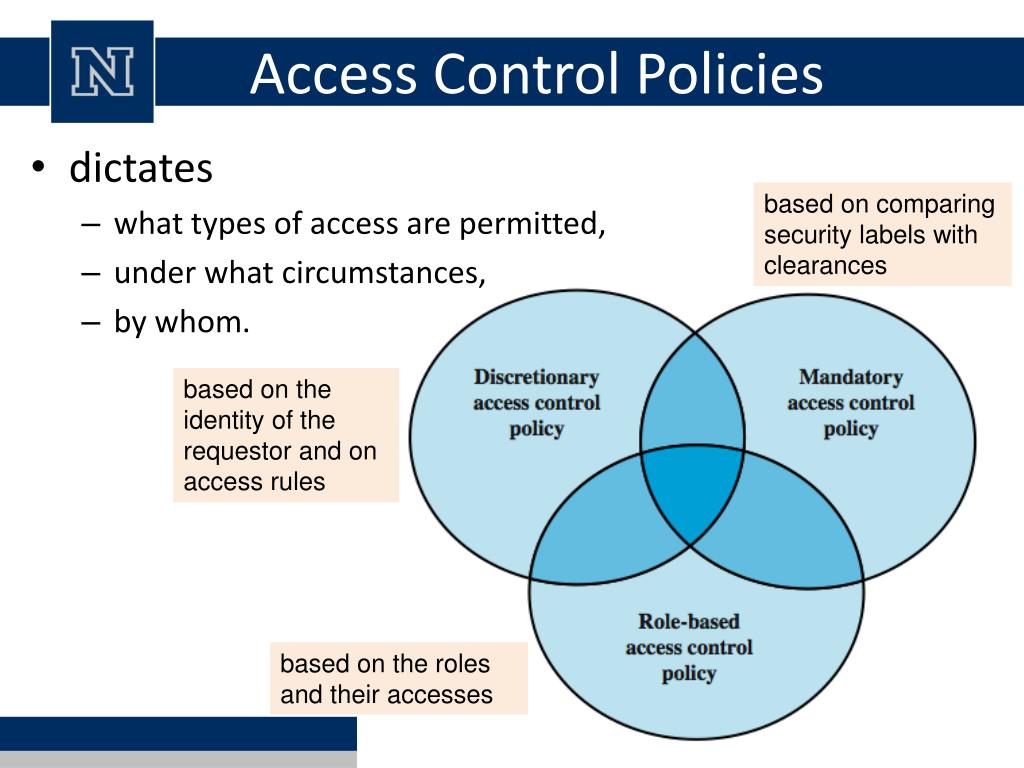
Access Control Policies Encryption . while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. access control encryption for general policies from standard assumptions. access control encryption for general policies from standard assumptions. Sam kim(b) and david j. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. while a number of access control encryption schemes exist, they either rely on strong assumptions such as. organizations planning to implement an access control system should consider three abstractions:
from www.slideserve.com
organizations planning to implement an access control system should consider three abstractions: access control encryption for general policies from standard assumptions. Sam kim(b) and david j. access control encryption for general policies from standard assumptions. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. while a number of access control encryption schemes exist, they either rely on strong assumptions such as.
PPT Lecture 7 Access Control PowerPoint Presentation, free download
Access Control Policies Encryption organizations planning to implement an access control system should consider three abstractions: encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. Sam kim(b) and david j. access control encryption for general policies from standard assumptions. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. access control encryption for general policies from standard assumptions. organizations planning to implement an access control system should consider three abstractions: while a number of access control encryption schemes exist, they either rely on strong assumptions such as.
From www.securityinfowatch.com
Access Control Encryption 101 Security Info Watch Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. access control encryption for general policies from standard assumptions. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. access control encryption for general policies from standard assumptions. Sam kim(b) and. Access Control Policies Encryption.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. Sam kim(b) and david j. access control encryption for general policies from standard assumptions. access control encryption for general policies from standard assumptions. while a number of access control encryption schemes exist, they either rely on strong assumptions. Access Control Policies Encryption.
From www.mdpi.com
Sensors Free FullText ProtocolBased and Hybrid Access Control for Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as. Sam kim(b) and david j. access control encryption for general policies from standard assumptions. organizations planning to implement an access control system should consider three abstractions: access control encryption for general policies from standard assumptions. encryption technology can. Access Control Policies Encryption.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. Sam kim(b) and david j. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. access control encryption for general policies from standard assumptions. organizations planning to implement an access control. Access Control Policies Encryption.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. Sam kim(b) and david j. organizations planning to implement an access control system should consider three abstractions: access control encryption for. Access Control Policies Encryption.
From www.scribd.com
Access Control Policy Template PDF Access Control Encryption Access Control Policies Encryption access control encryption for general policies from standard assumptions. access control encryption for general policies from standard assumptions. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. while a number of access control encryption schemes exist, they either rely on strong assumptions such as. organizations planning. Access Control Policies Encryption.
From www.securityinfowatch.com
Access Control Encryption 101 Security Info Watch Access Control Policies Encryption access control encryption for general policies from standard assumptions. access control encryption for general policies from standard assumptions. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. while a. Access Control Policies Encryption.
From www.slideserve.com
PPT Authentication and Authorization PowerPoint Presentation, free Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as. access control encryption for general policies from standard assumptions. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. access control encryption for general policies from standard assumptions. organizations planning to. Access Control Policies Encryption.
From homesecuritycamp.com
Encryption's Vital Role in Access Control Systems Access Control Policies Encryption encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. Sam kim(b) and david j. access control encryption for general policies from standard assumptions. organizations planning to implement an access control system should consider three abstractions: access control encryption for general policies from standard assumptions. while a number. Access Control Policies Encryption.
From www.slideshare.net
Security Policy and Key Management Centrally Manage Encryption Keys Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. access control encryption for general policies from standard assumptions. Sam kim(b) and david j. organizations planning to implement an access control system should consider three abstractions: while a number of access control encryption schemes exist, they either rely. Access Control Policies Encryption.
From eureka.patsnap.com
Cloud storage access control method based on attributebased encryption Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. Sam kim(b) and david j. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource.. Access Control Policies Encryption.
From store.cyberadviser.net
Access Control Policy CyberAdviser Store Access Control Policies Encryption organizations planning to implement an access control system should consider three abstractions: access control encryption for general policies from standard assumptions. while a number of access control encryption schemes exist, they either rely on strong assumptions such as. Sam kim(b) and david j. while a number of access control encryption schemes exist, they either rely on. Access Control Policies Encryption.
From www.researchgate.net
System model of attributebased access control for proxy reencryption Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. Sam kim(b) and david j. while a number of access control encryption schemes exist, they either rely on strong assumptions such as. access control encryption for general policies from standard assumptions. access control encryption for general policies from. Access Control Policies Encryption.
From www.slideserve.com
PPT CiphertextPolicy, AttributeBased Encryption PowerPoint Access Control Policies Encryption access control encryption for general policies from standard assumptions. encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. organizations planning to implement an access control system should consider three abstractions: Sam kim(b) and david j. while a number of access control encryption schemes exist, they either rely on. Access Control Policies Encryption.
From firewalltimes.com
Access Control Policy What to Include Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as. access control encryption for general policies from standard assumptions. organizations planning to implement an access control system should consider three abstractions: access control encryption for general policies from standard assumptions. encryption technology can be incorporated into access control. Access Control Policies Encryption.
From www.mdpi.com
Applied Sciences Free FullText An Improved CiphertextPolicy Access Control Policies Encryption access control encryption for general policies from standard assumptions. organizations planning to implement an access control system should consider three abstractions: while a number of access control encryption schemes exist, they either rely on strong assumptions such as. Sam kim(b) and david j. encryption technology can be incorporated into access control mechanisms based on user identities,. Access Control Policies Encryption.
From www.nextlabs.com
What is PolicyBased Access Control (PBAC)? NextLabs Access Control Policies Encryption encryption technology can be incorporated into access control mechanisms based on user identities, user attributes, or resource. while a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability. access control encryption for general policies from standard assumptions. access control encryption for general policies from standard assumptions. while a. Access Control Policies Encryption.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Access Control Policies Encryption while a number of access control encryption schemes exist, they either rely on strong assumptions such as. Sam kim(b) and david j. access control encryption for general policies from standard assumptions. organizations planning to implement an access control system should consider three abstractions: access control encryption for general policies from standard assumptions. encryption technology can. Access Control Policies Encryption.